25Feb2020
FedRAMP Deficiencies
This blog provides an overview of the Risk Management Framework (RMF) deficiencies impacting FedRAMP's approach as it pertains to 3rd Party Cloud Service Providers (CSPs).
DISCLAIMER: As someone who has worked with virtualization technologies since 2007 and someone who served as the Information Systems Security Officer (ISSO)/Security Engineer for one of the first government cloud systems to use a hybrid cloud deployment model in 2010, prior to FedRAMP being available to U.S. Government agencies, the information noted within isn't meant to denigrate nor disparage the FedRAMP team, but rather provide a professional input based on hands-on years of experience spent securing government systems and performing assessments on multiple government environments in accordance with NIST and Organizational Level guidance.
_________________
The FedRAMP process for assessing a cloud environment is based on the National Institute of Standards and Technology (NIST) guidance, with an emphasis on NIST 800-53 special publication. The NIST 800-53 publication delineates a set of controls that is tied to the NIST Risk Management Framework. While the FedRAMP process has integrated some changes, there are some key items that will lead to failures if not addressed correctly. Some of the issues include, but are not limited to, the following:
§ The process in itself has not been clearly molded to address risks specific to cloud environments as it pertains to Cloud Deployments, Cloud Models, and Cloud Technology Risks.
§ The focus of the assessments only address the Risk Management Framework Tier 3: Information Systems and fails to incorporate an assessment on the hosting's organization internal environment as it pertains to Tier 1 & Tier 2 risks.
Now- it is understood that FedRAMP has no saying on how the hosting environment addresses Tier 1 & Tier 2, because that is meant to be unique to each organization's environment and is outside of their control- and that is an issue. In fact, it is an issue for all parties involved, and can lead to hefty fines and major losses across the board
Therefore, we at CyberAdeptness believe that at the minimum, a hosting environment MUST be required to undergo a surface level Tier 1 & Tier 2 assessment to ensure that the Hosting environment being used to host certified FedRAMP systems can meet the government's risk appetite acceptance level for the agency. This will ensure that the agencies have:
- a more clear view of possible risks within the hosting environment,
- a clear view of possible Supply Chain issues; and
- an understanding of Internal/External Threats typically found within the hosting environments Tier 1 & Tier 2 levels.
As for the current approach, it is a can full of worms waiting to emerge in the upcoming future. Not only is this a can of worms, but such has also lead to a level of financial expenses that defy logic. You see... when the Risk Management Framework isn't applied correctly across the Enterprise, you will end up with the following issues:
§ Unnecessary and Bulky Compliance Paperwork,
§ Unnecessary Expenses and Acquisitions,
§ A False Sense of Security for all parties involved,
§ Undiscovered/Unknown CSP Perimeter and Organizational Risks due to lack of an organization-wide Risk Management Process, and
§ A false
sense of policies and procedures- for they only apply to FedRAMP systems but
not the Enterprise Systems used to develop, maintain, and manage the FedRAMP
environments.
While the above items aren't always obvious for many, it is for those of us who have spent many years securing and assessing government systems. The partial application of the NIST Risk Management Framework on non-government agencies is a recipe for disaster.
What kind of risks are impacting cloud environments?
Certainly, the risk depends on the hosting’s’ environment applicability of a Risk Management Framework, if any, or lack thereof. The following picture provides a high level overview on some of the issues that can impact the environment whenever the Risk Management Framework is not applied correctly:
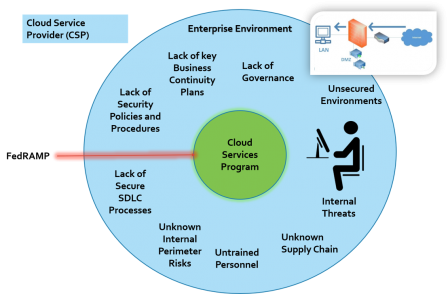
Issues Breakdown
- Lack of Security Policies and Procedures- It is a fact, that many CSPs develop FedRAMP documentation specific to address Tier 3: Information System's environments; however, 95% of the time, this policies do not apply to their own internal systems. In fact, most internal system wouldn't even meet a MOD Level Security Categorization Assessment.
- Lack of Business Continuity Plans- Many CSPs do not have an Enterprise Level Business Continuity Plan. The Plans developed for FedRAMP are specific to the systems and not the Enterprise environment. This means that if anything went wrong within their internal environment, the underlying environment can be impacted in the process.
- Lack of Secure SDLC Processes- Many CSPs are focus mainly on making money quickly and don't always incorporate security within their own SDLC process. In fact, it is non-existent for a high percentage of CSPs. This is especially true when it comes to their own internal developed systems process.
- Unknown Perimeter Risks- FedRAMP systems build by CSPs cannot address all Perimeter Risk within the organization, as they are only focused on Tier 3. This means that in some cases, the right security measures may be lacking at the perimeter, those leaving a high risk of unknown issues at the Enterprise Level. While many will argue that such wouldn't have an impact on a FedRAMP environment, we will argue that it does. It only takes one attack to disperse itself within all environments, including access to a "SECURED" environment managed via a semi-insecure environment.
- Untrained Personnel- When the FedRAMP process is applied by a CSP, the training developed is usually targeting only those who work within the FedRAMP environment. The issue is that- in most cases CSPs do not have an Enterprise Level Training Program for all other individuals within the organization. It takes ONE person within the organization for a cyber-attack to take place and impact the entire network.
- Unknown Supply Chain- Supply Chain issues aren't only tied to FedRAMP environments. In fact, they are usually tied up to the Enterprise environment and failure to grasp how Supply Chain is applied across the CSPs environments can lead to unknown risks.
- Internal Threats- When Tier 1 & Tier 2 Risk aren't identified, the risk for unknown internal risks is higher. Tier 3 assessments cannot fully identified internal CSP's internal threats.
- Lack of Governance- Failure to implement an Enterprise Level Risk Management Framework as a whole and/or incorrectly can lead to unidentified risks. This risk will have an impact on all parties involved, even the organization's consumers. FedRAMP Tier 3 cannot address all areas of the CSP's environments. It is the CSP's responsibilities to integrate an Enterprise Risk Management Framework that commensurate with FedRAMP's Risk Management Process- for it was developed in a manner that ties all areas into ONE.
- Unsecured Environments- CSP's implementing FedRAMP tend to focus on the FedRAMP environment only and fail to consider their own internal environment in the process. It is important to note that the CSP's internal environment is used to managed and architect FedRAMP environments, therefore, risks impacting the CSP's environment can have a major impact on a FedRAMP environment.
There's still time to address the deficiencies identified above. Certainly, the level of deficiencies will differ from CSP to CSP, as it is organization specific, but it seems to be an issue across many who believe that applying FedRAMP at the program level only is enough to protect the environment. That notion is wrong at many levels, because development of the architectural and security document and access to the secured environment starts from within the organizations boundary. If the organization's boundary isn't protected properly, an attacker and/or insider can gain access to the secured environment.
At the minimum, it's essential to understand the underlying deficiencies of CSPs. This can be determined by leveraging the Cybersecurity Framework Tiers which would provide a better picture of the ERA approach applied by the CSP's to address the underlying security processes not addressed at Tier 3.
What's the risk for CSP's and Government Agencies?
Failure to implement/integrate the Risk Management Framework organization-wide can have detrimental consequences for the provider and the consumer. The biggest risks for all parties is:
- costly legal litigations,
- costly security implementation expenses that defy logic,
- sensitive data and/or intellectual property leakage,
- civil penalties than can impact both entities, and
- damage to image or reputation of the organization(s) involved.
Conclusion
The FedRAMP’s process cannot be used as a checklist and cannot be relied upon as the
sole assessment to determine CSP level risks impacting their environment- mainly
because it DOES NOT address the underlying Tier 1 and Tier 2 risks. Tier 1
& Tier 2 risks MUST be identified, and such process falls greatly on the
CSP provider.
It's highly advisable that all organizations, regardless of size and budget, serious about limiting cyber-attacks, undergo an Enterprise Level Risk Assessment in order to identify all risks and deficiencies impacting not only the organization internally, but also its consumers and 3rd Party Service Providers.
This will provide a better idea of risks across the organization and whether or not the organization is willing to accept the risk identified and/or develop a plan to prioritize the remediation process.
If you’re a CSP that host FedRAMP systems and/or plans to host FedRAMP systems- you should, at the minimum, consider a Tier 1 and Tier 2 Risk Management Assessment. If you wish to learn more- Contact Us.